Protect Yourself Against New ID-Theft Schemes
Crooks are using more-sophisticated tricks to steal your data. It's time to improve your armor.


Profit and prosper with the best of Kiplinger's advice on investing, taxes, retirement, personal finance and much more. Delivered daily. Enter your email in the box and click Sign Me Up.
You are now subscribed
Your newsletter sign-up was successful
Want to add more newsletters?

Delivered daily
Kiplinger Today
Profit and prosper with the best of Kiplinger's advice on investing, taxes, retirement, personal finance and much more delivered daily. Smart money moves start here.

Sent five days a week
Kiplinger A Step Ahead
Get practical help to make better financial decisions in your everyday life, from spending to savings on top deals.

Delivered daily
Kiplinger Closing Bell
Get today's biggest financial and investing headlines delivered to your inbox every day the U.S. stock market is open.

Sent twice a week
Kiplinger Adviser Intel
Financial pros across the country share best practices and fresh tactics to preserve and grow your wealth.

Delivered weekly
Kiplinger Tax Tips
Trim your federal and state tax bills with practical tax-planning and tax-cutting strategies.

Sent twice a week
Kiplinger Retirement Tips
Your twice-a-week guide to planning and enjoying a financially secure and richly rewarding retirement

Sent bimonthly.
Kiplinger Adviser Angle
Insights for advisers, wealth managers and other financial professionals.
Sent twice a week
Kiplinger Investing Weekly
Your twice-a-week roundup of promising stocks, funds, companies and industries you should consider, ones you should avoid, and why.

Sent weekly for six weeks
Kiplinger Invest for Retirement
Your step-by-step six-part series on how to invest for retirement, from devising a successful strategy to exactly which investments to choose.
Throughout the past decade, consumers have been rocked by one massive data breach after another. Some 500 million Yahoo users were hit by a 2014 data breach that compromised e-mail addresses, passwords and other information. The 2017 hack of credit bureau Equifax exposed Social Security numbers and other sensitive information of 147 million people. Thousands of other breaches exposed the data of millions of consumers, who have come to assume that their personal data has been laid bare somewhere.
Lately, however, fraudsters have shifted from large-scale hacks to more-focused attacks—on businesses in particular. In 2020, the total number of data breaches dropped by 19% compared with 2019, according to the Identity Theft Resource Center. “Ransomware and phishing attacks directed at organizations are now the preferred method of data theft by cyberthieves,” the ITRC wrote in its 2020 Data Breach Report. The ransomware strategy, through which criminals encrypt data on a network computer and then demand that you pay for a key to decrypt it, received much attention after hackers forced down Colonial Pipeline, a major supplier of gasoline and jet fuel in the Southeast.
That creates greater impetus for organizations to protect themselves and their employees, but consumers still have plenty of reason to stay on guard in their personal lives, too. Identity thieves haven’t given up on data breaches. Plus, your Social Security number and date of birth are unchanging bits of information that criminals can use years after stealing them to carry out crimes such as opening a new credit account or filing a tax return in your name. And crooks continue to capitalize on current events—especially those involving health, the economy, holidays and disasters—to wring money or personal information from victims, says Adam Levin, founder of identity-protection service CyberScout. Increasingly, criminals are contacting consumers directly using scams designed to draw out personal information, and victims now often recall the moment they interacted with a criminal text, call or e-mail, rather than having no idea how their identity was stolen, according to Javelin Strategy & Research.
From just $107.88 $24.99 for Kiplinger Personal Finance
Become a smarter, better informed investor. Subscribe from just $107.88 $24.99, plus get up to 4 Special Issues

Sign up for Kiplinger’s Free Newsletters
Profit and prosper with the best of expert advice on investing, taxes, retirement, personal finance and more - straight to your e-mail.
Profit and prosper with the best of expert advice - straight to your e-mail.
We’ve outlined how you can defend against several types of fraud, as well as the steps to take if you become a victim. The Identity Theft Resource Center offers free victim assistance through its hotline at 888-400-5530. And at IdentityTheft.gov, you can fill out an identity theft report (you may have to submit it to businesses involved in your ID theft claim to prove that you’re a victim) and launch a recovery plan.
Phishing schemes
The problem: Through e-mails and text messages, criminals contact consumers and pose as legitimate institutions—say, the IRS, the Social Security Administration, a bank or a well-known business—in attempts to gain personal information or money. You may, for example, receive a fake e-mail requesting that you provide your credit card information to continue receiving service from a utility or other entity or advising you to click on a link to reset your account password.
How to protect yourself: Make sure you know the signs of a phishing e-mail or text message. Less-sophisticated attempts aren’t terribly difficult to spot—they often include spelling and grammatical errors, use a formal or generic greeting, and attempt to invoke a sense of urgency for you to take action. Even if an e-mail looks legitimate, check the sender’s e-mail address; if the domain doesn’t seem to match the business from which the message claims to originate, or if it’s from a personal service such as Gmail.com or Yahoo.com, the e-mail is likely fraudulent. Look closely at a domain that appears genuine at first glance, too—it may, for example, include the number zero where the letter O should be.
Don’t click on website links or enable downloads within the message—if you do, you may install malware on your device or be directed to a scam website that mimics a real one. Hover your cursor over links to see their true destinations (the web address will pop up on your screen). If you’re unsure whether an e-mail or text message is legitimate, look up the phone number of the sender it purports to be from and call to ask whether the message is real.
Some phishing attempts are more advanced—and harder to identify. “Spear-phishing” targets specific individuals and may leverage information that the fraudster has obtained about the recipient—from his or her social media profiles, for example—making the message seem more authentic. The message may greet you by your name and include a signature with the name of a friend or work colleague. If the message has an off-kilter tone or includes an unexpected or unusual request, there’s a good chance it’s fake.
What to do if you’re a victim: Take stock of what information was compromised. If you realize that you gave away the log-in information to one of your accounts—say, because you followed a link to a scam website that looks like that of your bank and entered the credentials—reset your password for that account and any others for which you use the same log-in information. If you handed over your credit card or bank account number, notify the institution immediately. In case your device is infected with malware, run a scan from a service such as Malwarebytes to clean up. (See below for more on securing your passwords, payment accounts, sensitive personal information and devices.) Did you fall prey to a phishing scheme at work? Alert your employer’s information-technology department right away.
Vulnerable devices
The problem: Your smartphone and computer are vulnerable to both physical theft and online assaults, such as through viruses, ransomware and compromised Wi-Fi. Other devices in your home that are connected to the internet, such as security cameras and smart speakers, are subject to hacking as well.
How to protect yourself: One of the most important actions you can take is to install updates for the operating system and software on your devices as soon as you receive a notification to do so. The updates may include patches to fix security flaws. Use an antivirus program to shield your computer from attacks. And before you put software on your computer or an app on your smartphone, make sure it’s from a reputable source.
As the gas shortages of the Colonial Pipeline attack made vivid, Ransomware has increasingly become a threat to businesses, which have deeper pockets than most individuals. Still, “ransomware hits consumers all the time,” says Alex Hamerstone, advisory solutions director for cybersecurity firm TrustedSec. The best defense is to regularly back up files stored on your computer to a second source. You could use a cloud-based server or an external hard drive—but be sure to disconnect an external drive when you’re not backing up files or hackers could encrypt it, too, says Randy Pargman, vice president of threat hunting and counterintelligence for cybersecurity firm Binary Defense.
It’s not a bad idea to isolate your most sensitive transactions, such as managing bank accounts and insurance, to a separate device from ones that you or your family members use to, say, play games or watch videos, says Mark Ruchie, chief information security officer for security firm Entrust. Those activities may invite malware. Change the default passwords that come with your internet router and smart devices.
When you are outside your home, avoid hooking up to public Wi-Fi, through which hackers could access your device, and turn off your device’s Bluetooth connection. If you regularly use the internet on your computer while you’re on the go, consider using a VPN, which provides an encrypted connection. In case a thief swipes your laptop or smartphone, secure the home screen with a password, PIN, pattern or biometric authenticator (such as your fingerprint), and password-protect banking and other sensitive applications within your phone, too.
What to do if you’re a victim: If your smartphone is stolen, remotely erase its data. (Before your device goes missing, turn on within its settings “Find My Device” with an Android phone or “Find My iPhone” with an iPhone.) If you’re an Android user, go to www.android.com/find, where you can sign in to your Google account and choose to delete the device’s content. Act quickly—the phone must be turned on and online for the feature to work. With an Apple device, log in to www.icloud.com/find and erase the data with Find My iPhone. Your iPhone must be online; if it is offline, the contents will be erased the next time it is online.
Ransomware victims may be able to find keys to decrypt their data with a web search or by visiting www.nomoreransom.org. Otherwise, you have to decide whether it’s worth paying to get your data back. “We don’t advise people or businesses on whether to pay the ransom because we understand that’s a hard choice to make,” says Eva Velasquez, president and CEO of the Identity Theft Resource Center. But keep in mind that paying the ransom reinforces the business model for fraudsters, and there’s no guarantee that they’ll return your data after you pay. In a survey from cybersecurity company Kaspersky, 17% of respondents who paid a ransom didn’t get their data back.
Antivirus software can help you detect and remove malware from your device. The AV-TEST Institute, which runs tests on antivirus software, recently deemed Bitdefender Internet Security (from $32 to $89.99 the first year, depending on the number of devices) and F-Secure SAFE ($34.99 to $139.99 a year, depending on the number of devices) as the programs with the best protection for consumers. Among free software, check out Bitdefender Antivirus Free Edition and Kaspersky Security Cloud Free.
If you need more help, hire a pro. Best Buy’s Geek Squad, for example, offers virus and spyware removal for $150.
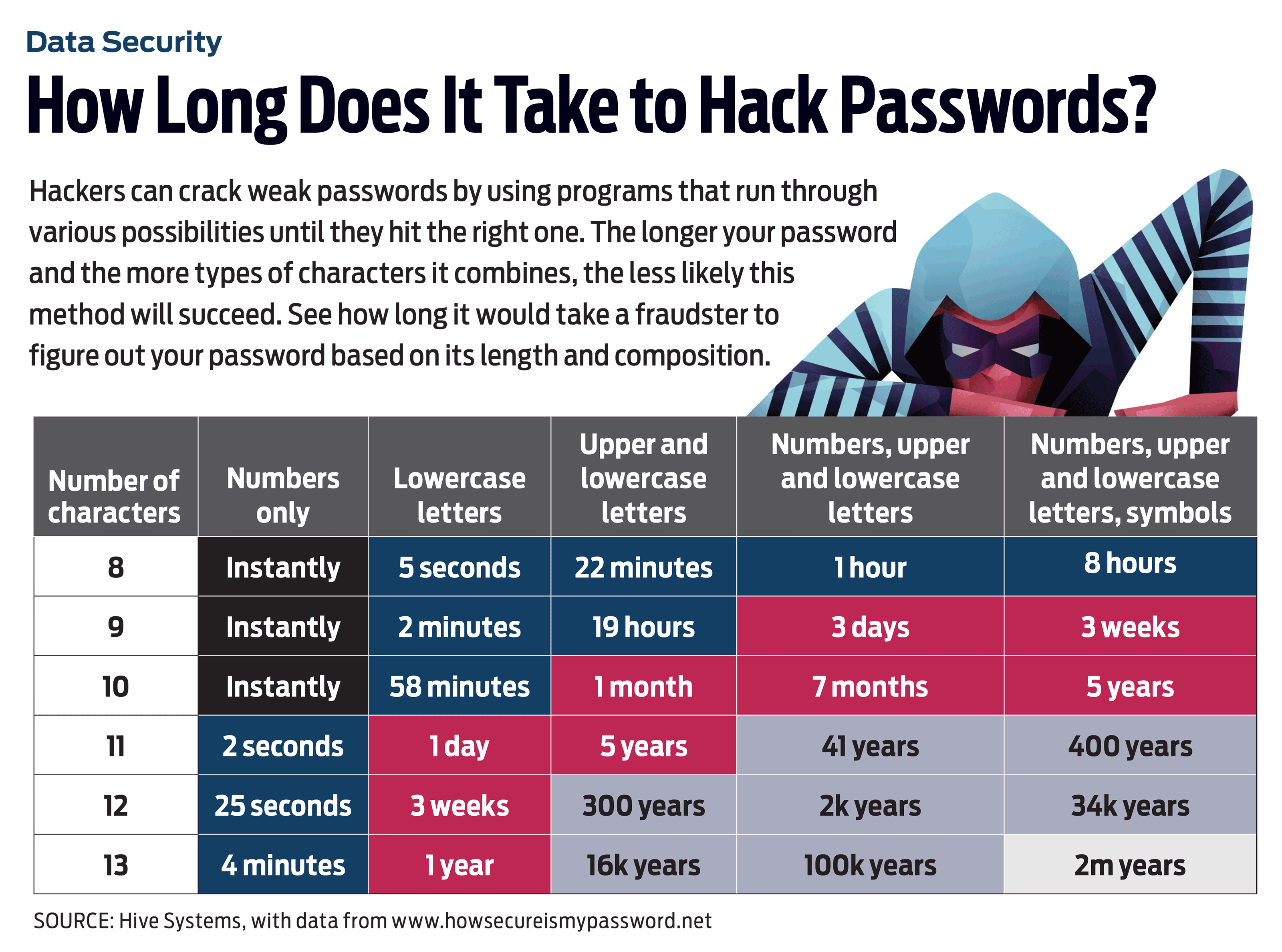
Hacked passwords
The problem: Creating strong passwords and remembering them is a heavy lift without some help, and many consumers fall into bad habits; in 2020, the most common password was “123456,” according to password manager NordPass. If you reuse the same password on multiple accounts, a crook who grabs your log-in credentials for one website can use them to access other sites.
How to protect yourself: “Good password management is one of the best risk-minimization steps people can take. I can’t say that enough,” says Velasquez. A password manager—such as Dashlane, Keeper or LastPass—is a great tool to securely store log-in credentials and to generate strong, unique passwords for each account.
“Human-generated passwords are normally very weak,” says Fleming Shi, chief technology officer for security service Barracuda. Some programs offer a free, basic version that manages passwords on a single device as well as advanced options that provide management on multiple devices and other features for a monthly fee. LastPass, for example, is free for one user with one device, $3 monthly for one user with unlimited devices or $4 monthly for up to six users with unlimited devices. Paid accounts come with extras such as 1 gigabyte of file storage, as well as monitoring of internet black-market sites for your personal information. Your web browser may offer password management, but dedicated programs are typically more powerful and provide more features.
If you’re creating a password without assistance from a program, choose a password with at least 12 characters, says Velasquez. Using both uppercase and lowercase letters is a good idea, too. You don’t have to string together a nonsensical sequence of characters for the password to be secure. Instead, put together a “passphrase” by combining a few words—say, from a favorite song or quote. You could choose a core passphrase and alter it for each account to ensure unique credentials for each site, says Velasquez.
Add a layer of security by using multifactor authentication whenever possible. A website, for example, may send you a code by text message or e-mail when there’s an attempt to log in from an unfamiliar device and require you to enter the code for access.
What to do if you’re a victim: If you find out that your log-in credentials have been compromised, immediately change your password on the affected account. If you use the same password on any other accounts, change those, too (and choose unique passwords for each account this time). At www.haveibeenpwned.com, you can look up your e-mail address to see whether it and your passwords have been involved in any data breaches.
Compromised payments
The problem: Since the U.S. moved toward credit card and debit card transactions involving a microchip and contactless payment technology, counterfeit-card fraud has plummeted. But criminals can still snag payment information online—by compromising merchant websites, for example. And in 2020, fraud involving digital wallets and peer-to-peer payment services victimized nearly 18 million people, according to Javelin.
How to protect yourself: Avoid storing your payment information on retailer websites—it could be stolen if a hacker digs into the system. Some financial institutions, including Capital One and Citi, offer eligible cardholders the option of using a virtual card number for online purchases. The temporary virtual numbers differ from your real account number, sheltering it from fraud. When possible, access your bank account through the bank’s mobile app rather than logging in on a web browser—the app’s security features tend to be stronger, says Tracy Kitten, director of fraud and security practice for Javelin.
Check your bank and credit card accounts at least weekly—or even better, daily—for unauthorized purchases, and sign up for e-mail, text-message or mobile-app alerts from your financial institutions notifying you each time there’s a transaction on your credit and debit cards. When possible, make purchases with a credit card—it has stronger liability protections than a debit card.
Fraud involving peer-to-peer payment services, such as PayPal and Venmo, is often tied to scams in which criminals persuade victims to send them money. Before you transfer cash with a mobile service, verify that the recipient is someone you know and trust. Keep your Venmo transactions private rather than allowing them to be displayed publicly, says Liz Lasher, a vice president for credit-score company FICO. Crooks could take note of your transaction patterns, use the information to set up a fake profile that looks like yours and request money from your friends.
What to do if you’re a victim: If you notice unauthorized transactions on your credit or debit account, contact your financial institution immediately. It can block any further transactions and send you a card with a new number. Some issuers allow you to log in to your account online and switch the card off, rendering it unusable, if you’ve lost it or suspect theft. If you later find a lost card or discover that it has not been compromised, you can reactivate it.
Be aware of your liability protections under federal law. With a credit card, you will owe no more than $50 for unauthorized usage—and your liability is zero if the card number but not the card itself is stolen. With a debit card, it depends on how quickly you report theft; you won’t be held liable if your card number is used for unauthorized purchases (but the card itself hasn’t been stolen) as long as you report the charges within 60 days. If your card is physically lost or stolen, your liability could be unlimited if you wait more than 60 days to notify the bank of unauthorized charges; otherwise, liability is $500 or less.
Stolen Social Security numbers
The problem: Your Social Security number is the key that criminals need to wreak havoc on your identity. By piecing it together with other bits of your personal information, such as your name and date of birth, they could open new credit accounts in your name, file a false tax return to collect a refund, apply for unemployment benefits, receive medical care or rent an apartment—complete with utilities.
How to protect yourself: There’s not much you can do about institutional data breaches that reveal your SSN and other personal information to bad actors. But you can take steps to protect it in your everyday life. Don’t carry your Social Security card in your wallet, and shred unneeded documents that include your SSN. Be wary of giving away your SSN; government and financial institutions often have valid reasons to request it, but not all organizations need to use or store it. Binary Defense’s Pargman says that when a volunteer organization used his SSN and birth date for a background check, upon his request it agreed to remove the data from its records after the check was complete.
A credit freeze is the most effective way to prevent criminals from using your SSN to open new credit card or loan accounts in your name. When a freeze is in place, lenders cannot check your credit report in response to a request for new credit. Contact each of the three major credit bureaus—Equifax, Experian and TransUnion—to freeze your reports (for a step-by-step guide, visit kiplinger.com/links/freeze). You can freeze the credit records of your minor children and for individuals (such as elderly parents) for whom you’re a guardian or conservator or have a power of attorney.
The IRS recently began allowing all taxpayers—not just identity-theft victims—to get an Identity Protection (IP) PIN. If you sign up for one (go to www.irs.gov/ippin), you must provide it when you file your taxes. A fraudster who attempts to submit a tax return in your name will fail without the PIN.
In case a thief manages to use your SSN or health insurance information to get medical care, review all insurance explanations of benefits, and watch for bills for care you never received.
What to do if you’re a victim: Keep a close eye on your credit reports. Through April 20, 2022, the three major credit bureaus are offering free reports on a weekly basis—rather than the usual once per 12 months—at www.annualcreditreport.com. You can also get alerts of significant changes to your credit reports through services such as CreditKarma.com and FreeCreditScore.com. If you notice anything suspicious, such as the presence of a credit account you never opened or a collection account for a debt you don’t owe, contact the lender or other entity that furnished the fraudulent or erroneous information, and file a dispute with each bureau reporting it (see How to Fix Your Credit Report). If you’re a victim of tax-related ID theft, fill out and submit IRS Form 14039. The IRS will investigate your case and send you a notification once it is resolved.
Profit and prosper with the best of Kiplinger's advice on investing, taxes, retirement, personal finance and much more. Delivered daily. Enter your email in the box and click Sign Me Up.

Lisa has been the editor of Kiplinger Personal Finance since June 2023. Previously, she spent more than a decade reporting and writing for the magazine on a variety of topics, including credit, banking and retirement. She has shared her expertise as a guest on the Today Show, CNN, Fox, NPR, Cheddar and many other media outlets around the nation. Lisa graduated from Ball State University and received the school’s “Graduate of the Last Decade” award in 2014. A military spouse, she has moved around the U.S. and currently lives in the Philadelphia area with her husband and two sons.
-
 Dow Leads in Mixed Session on Amgen Earnings: Stock Market Today
Dow Leads in Mixed Session on Amgen Earnings: Stock Market TodayThe rest of Wall Street struggled as Advanced Micro Devices earnings caused a chip-stock sell-off.
-
 How to Watch the 2026 Winter Olympics Without Overpaying
How to Watch the 2026 Winter Olympics Without OverpayingHere’s how to stream the 2026 Winter Olympics live, including low-cost viewing options, Peacock access and ways to catch your favorite athletes and events from anywhere.
-
 Here’s How to Stream the Super Bowl for Less
Here’s How to Stream the Super Bowl for LessWe'll show you the least expensive ways to stream football's biggest event.
-
 9 Types of Insurance You Probably Don't Need
9 Types of Insurance You Probably Don't NeedFinancial Planning If you're paying for these types of insurance, you may be wasting your money. Here's what you need to know.
-
 The 'Scrooge' Strategy: How to Turn Your Old Junk Into a Tax Deduction
The 'Scrooge' Strategy: How to Turn Your Old Junk Into a Tax DeductionTax Deductions We break down the IRS rules for non-cash charitable contributions. Plus, here's a handy checklist before you donate to charity this year.
-
 When Tech is Too Much
When Tech is Too MuchOur Kiplinger Retirement Report editor, David Crook, sounds off on the everyday annoyances of technology.
-
 Seven Things You Should Do Now if You Think Your Identity Was Stolen
Seven Things You Should Do Now if You Think Your Identity Was StolenIf you suspect your identity was stolen, there are several steps you can take to protect yourself, but make sure you take action fast.
-
 The 8 Financial Documents You Should Always Shred
The 8 Financial Documents You Should Always ShredIdentity Theft The financial documents piling up at home put you at risk of fraud. Learn the eight types of financial documents you should always shred to protect yourself.
-
 How to Guard Against the New Generation of Fraud and Identity Theft
How to Guard Against the New Generation of Fraud and Identity TheftIdentity Theft Fraud and identity theft are getting more sophisticated and harder to spot. Stay ahead of the scammers with our advice.
-
 12 Ways to Protect Yourself From Fraud and Scams
12 Ways to Protect Yourself From Fraud and ScamsIdentity Theft Think you can spot the telltale signs of frauds and scams? Follow these 12 tips to stay safe from evolving threats and prevent others from falling victim.
-
 Watch Out for These Travel Scams This Summer
Watch Out for These Travel Scams This SummerIdentity Theft These travel scams are easy to fall for and could wreck your summer. Take a moment to read up on the warning signs and simple ways to protect yourself.